The Windows Server Update Services (WSUS) and I have one thing in common: neither of us likes change. For myself, I believe this hesitation adds to my charm and shows that I value stability. For WSUS, it means a lack of new features and changes that sysadmins have requested for years.
While WSUS might be stuck in its ways, PDQ is always looking to add value to its products, including improving the Windows update process. To that end, we’ve added several new packages to the Package Library in PDQ Deploy and PDQ Connect. Their goal? To help sysadmins identify, distribute, and manage Windows updates on their endpoints. Let’s look at these new packages and see how they can help you replace or at least minimize your use of WSUS.
Meet the new PSWindowsUpdate packages
To help sysadmins better administer Windows updates, PDQ has added six new packages to PDQ Deploy and five packages to PDQ Connect, all of which can be found using the filter PSWindowsUpdate.
PSWindowsUpdate – Get All Applicable Updates from Microsoft (Audit Only)
PSWindowsUpdate – Install All Applicable Updates from Microsoft (No Drivers, No Feature Updates)
PSWindowsUpdate – Install Applicable Critical and Security Updates from Microsoft
PSWindowsUpdate – Install Applicable Drivers from Microsoft
PSWindowsUpdate – Install Applicable Feature Updates from Microsoft
PSWindowsUpdate – Install Specific Microsoft KB
The Install Specific Microsoft KB package is currently only available in PDQ Deploy. However, I’ll show you how to manually add this package to PDQ Connect later in this article.
Easily run PowerShell scripts on remote devices
Need to run your awesome PowerShell scripts on remote devices? PDQ Connect can easily execute PowerShell scripts on any managed device with an active internet connection.
What is PSWindowsUpdate?
PSWindowsUpdate is a very popular PowerShell module with over 300 million downloads, making it the second most downloaded module from the PowerShell Gallery. Authored by Microsoft MVP and accomplished sysadmin Michal Gajda, PSWindowsUpdate is designed to help sysadmins administer Windows updates via PowerShell.
How does PDQ leverage PSWindowsUpdate?
PDQ Deploy and Connect specialize in deploying applications, updates, and scripts to endpoints. By leveraging the PSWindowsUpdate module, these new packages contain a PowerShell script that can identify and install missing patches on managed devices.
It’s important to note that the updates are not pushed out by PDQ Deploy or Connect. Instead, the package backs up existing WSUS settings, downloads updates directly from Microsoft online servers, then restores WSUS settings when finished.
Updates are specific per machine, meaning the same package deployed to multiple endpoints may download different patches, depending on the architecture, OS, and needs of each device. Because updates are downloaded directly from Microsoft, these packages don’t work on air-gapped networks.
Breaking down each of the new packages and what they do
With six new packages all utilizing the PSWindowsUpdate module, you may be wondering what makes each package unique and when to use one over another. Good question. While every package provides a descriptive name, let’s briefly go over what each does and when you should utilize it.
PSWindowsUpdate – Get All Applicable Updates from Microsoft (Audit Only)
Out of all the PSWindowsUpdate packages, this is the only one that doesn’t install anything. The Get All Applicable Updates from Microsoft (Audit Only) package is designed to identify missing updates applicable to the target machine. Specifically, this package returns identified missing updates to the output log.
This package might be my favorite of the bunch because accurate information is incredibly valuable and leads to decisive decisions. Here’s how it works:
Deploy the package to an endpoint.
When the deployment finishes, click on the Steps link.
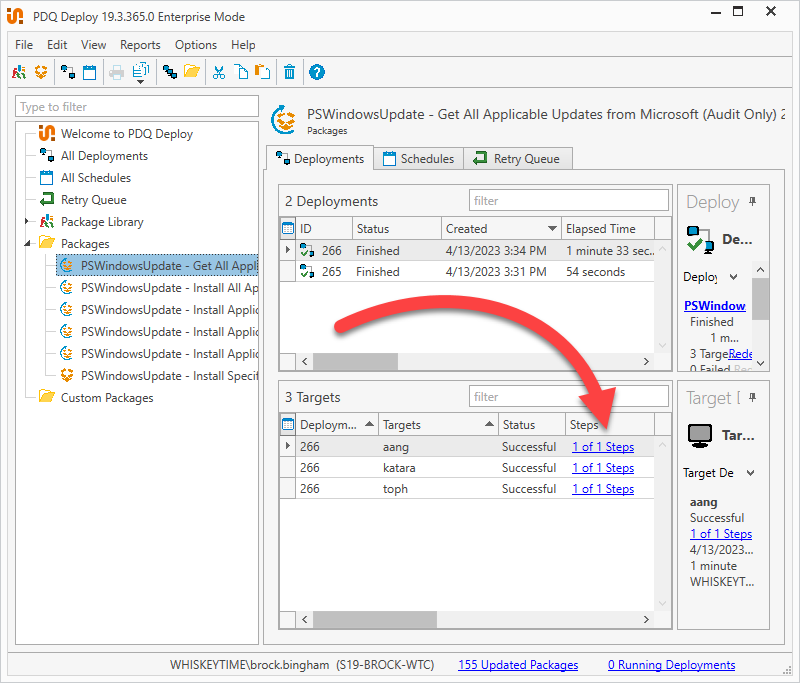
Click on the Output Log link.
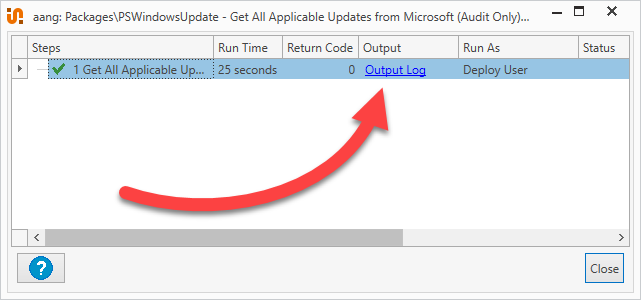
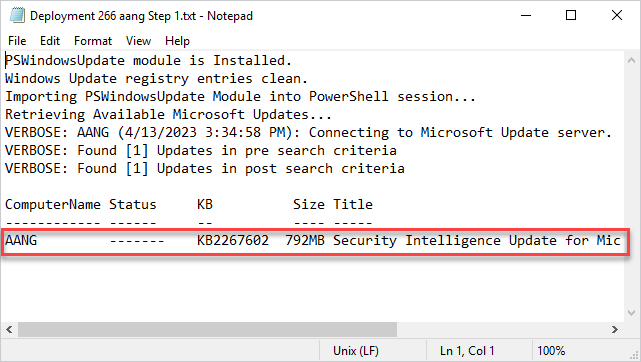
At the bottom of the output log, you’ll find a list of the missing updates available for that device.
PSWindowsUpdate – Install All Applicable Updates from Microsoft (No Drivers, No Feature Updates)
This package will install all applicable updates from Microsoft, excluding driver and feature updates. If your primary concern is ensuring endpoints are up to date with the most relevant patches, this is the package for you.
PSWindowsUpdate – Install Applicable Critical and Security Updates from Microsoft
Cybersecurity threats are on the rise. Shocking, I know. Unfortunately, this trend will only worsen as businesses become more reliant on online infrastructure, remote work, and IoT devices. While there are several cybersecurity practices that companies should implement to protect against cyberthreats, one of the most important ways an organization can defend against threats like ransomware is to ensure endpoints are up to date with critical and security updates.
This package is designed to help sysadmins ensure devices have the most recent critical and security updates applied. It ignores noncritical updates to ensure you have enough time to properly test them before distributing them to your endpoints.
PSWindowsUpdate – Install Applicable Drivers from Microsoft
As the name suggests, if you need to install driver updates, this is the package for you. From years of experience deploying driver updates, I recommend updating drivers in small batches. In my experience, driver updates can be finicky, for lack of a better term. It may also be beneficial to group devices by make and model before updating drivers.
PSWindowsUpdate – Install Applicable Feature Updates from Microsoft
Feature updates are the heavyweights of the Microsoft update catalog. While quality updates include things such as bug fixes, vulnerability patches, and stability improvements, feature updates are new versions of the operating system, often introducing new features and significant changes to the OS.
Deploying feature updates should always be done with caution. Give yourself plenty of time to test feature updates and ensure they don’t cause compatibility issues with your systems. I advise deploying feature updates to a pilot group.
It’s important to remember that feature updates can be several GBs in size and take a long time to install. Keep bandwidth limitations in mind, and consider deploying feature updates after hours to avoid conflicting with user schedules. This is another package you’ll want to deploy to small groups of devices.
PSWindowsUpdate – Install Specific Microsoft KB
If you’ve ever found yourself in a situation where you need to get specific patches deployed in a hurry (ahem, pretty much every Patch Tuesday), then this package will be your new best friend.
The Install Specific Microsoft KB package allows you to specify the KBs you wish to install on your endpoints. This package is extremely handy for those zero-day patch deployments. Here’s how it works:
Double-click on the PSWindowsUpdate – Install Specific Microsoft KB package.
Click on the Step 1 – Install Specific Microsoft KB step.
Enter the KB number you wish to install in the Parameters field. You can enter multiple KB numbers, separating them by commas and enclosing everything in single quotes. (Example: -KBArticleID ‘KB8675309,KB9035768,KB1234567’)
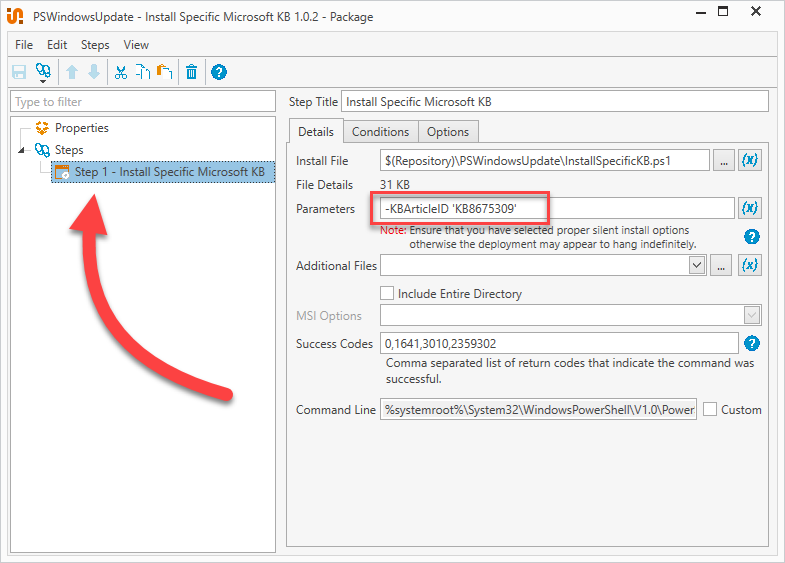
Click the Save button to save the package.
Close the package.
Once you’ve entered the KB numbers, your package is ready to deploy to your endpoints.
The reason this package isn’t included with PDQ Connect is because Connect currently doesn’t provide a way for users to modify parameters of prebuilt packages. Not to worry — we can manually build this package in Connect in just a few steps.
In PDQ Connect, click Packages, then click Create package.
Name the package.
Click the Add install step dropdown button, then click the Add PowerShell step option.
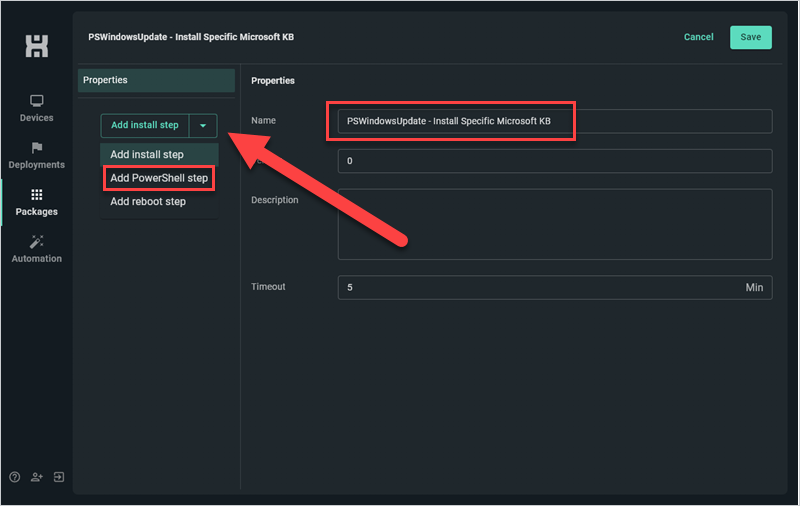
Add this script into the command window:
[CmdletBinding()] param ( [Parameter(Mandatory = $true)] [String]$KBArticleID ) Write-Host "KBArticleID is $KBArticleID" $Module = "PSWindowsUpdate" $RegPath = "HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate" IF(Get-Module -ListAvailable -Name $Module){ Write-Host "$Module module is Installed." } ELSE{ Write-Host "$Module module is Not Installed." Write-Host "Installing NuGet Package Installer..." [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 Install-PackageProvider -Name NuGet -MinimumVersion 2.8.5.201 -Force -confirm:$False Write-Host "Installing $Module Module..." Install-Module -Name $Module -Force -Confirm:$False } IF(Test-Path $RegPath){ Write-Host "$RegPath Exists." Write-Host "Removing Old Windows Update registry entries..." Stop-Service -Name wuauserv Remove-Item $RegPath -Recurse Start-Service -name wuauserv Write-Host "Windows Update registry entries clean." } ELSE{ Write-Host "Windows Update registry entries clean." } Write-Host "Importing $Module Module into PowerShell session..." Import-Module $Module Write-Host "Retrieving Available Microsoft Updates..." Get-WindowsUpdate -MicrosoftUpdate -Verbose Write-Host "Installing Selected Updates..." Install-WindowsUpdate -MicrosoftUpdate -AcceptAll -Verbose -IgnoreReboot -KBArticleID $KBArticleIDAdd -KBArticleID ‘KB8675309’ to the Parameters field.
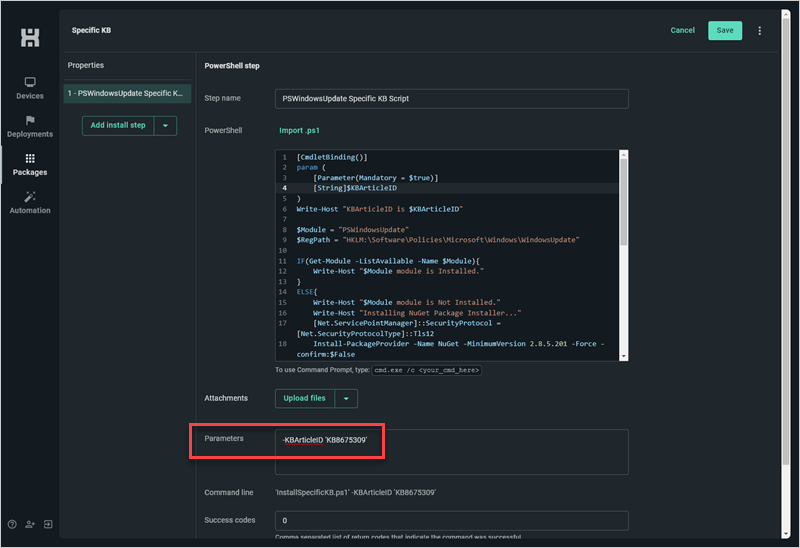
Click Save to save the package.
With the package saved, simply modify the KB numbers in the Parameters field with the KB numbers you need to install before deploying the package.
Manage your remote and on-prem endpoints with ease
PDQ Connect and Deploy & Inventory make device management simple.
Enhancing PDQ Inventory with a PSWindowsUpdate scanner and report
Not one to be left out, PDQ Inventory can also take advantage of these new packages. In the PSWindowsUpdate – Get All Applicable Update from Microsoft (Audit Only) package, you'll find two XML files you can import into PDQ Inventory to add a new Windows update PowerShell Scanner and report.
Here's how to import the scanner into PDQ Inventory:
Right-click on the Scan Profiles button in PDQ Inventory, then click Import.
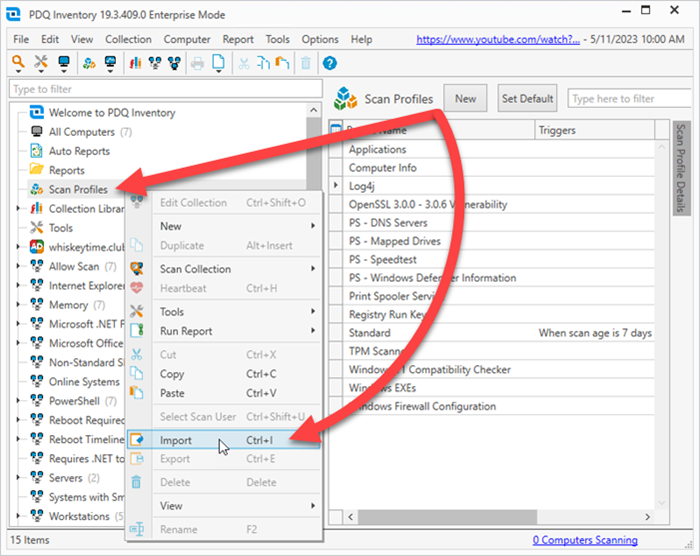
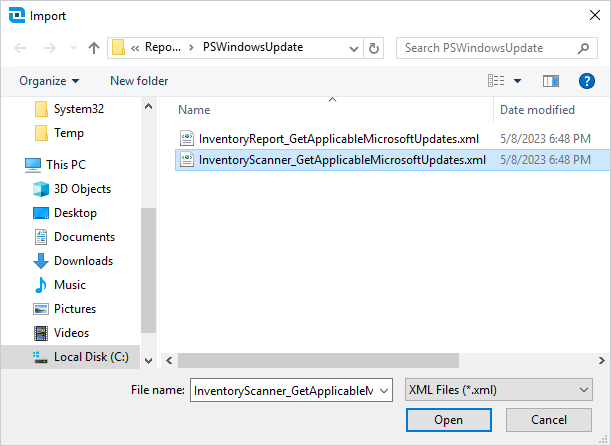
Browse to the scanner XML located at $(Repository)\PSWindowsUpdate\InventoryScanner_GetApplicableMicrosoftUpdates.xml
Select the XML, then click Open.
Optional step: If your environment requires signed PowerShell scripts, you can remove the script imported with the XML file and point to the included PowerShell file located in the same directory as the XML files.
Once the new scan profile is imported into Inventory, you’ll find it under your list of available scan profiles.
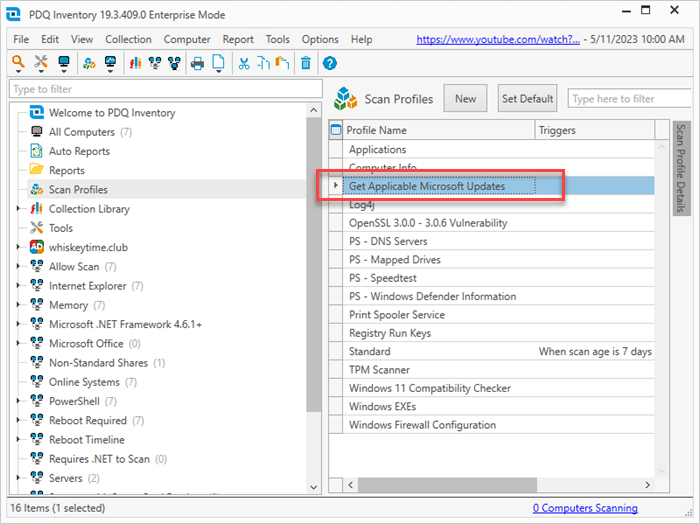
To run the scanner against your computers in Inventory, right-click on All Computers, then click Scan Collection > Get Applicable Microsoft Updates.
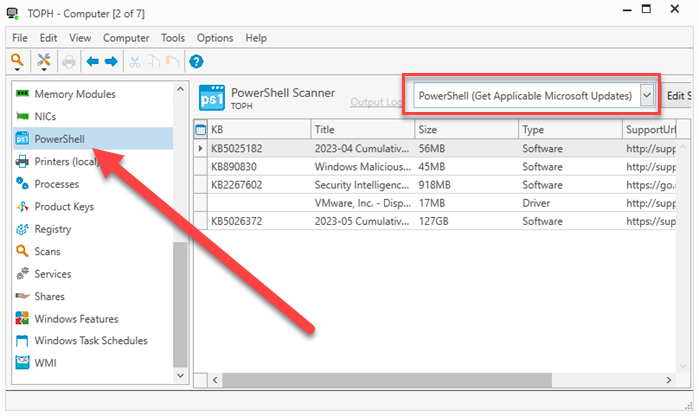
After the scan finishes, double-click on a device in Inventory to open the device details window, then select the PowerShell option from the menu on the left. Finally, click the PowerShell Scanner drop-down menu option, and select the PowerShell (Get Applicable Microsoft Updates) scanner.
Now that we have the results from the scan, we can add a report to Inventory to track this information by importing the Get Applicable Microsoft Updates report XML.
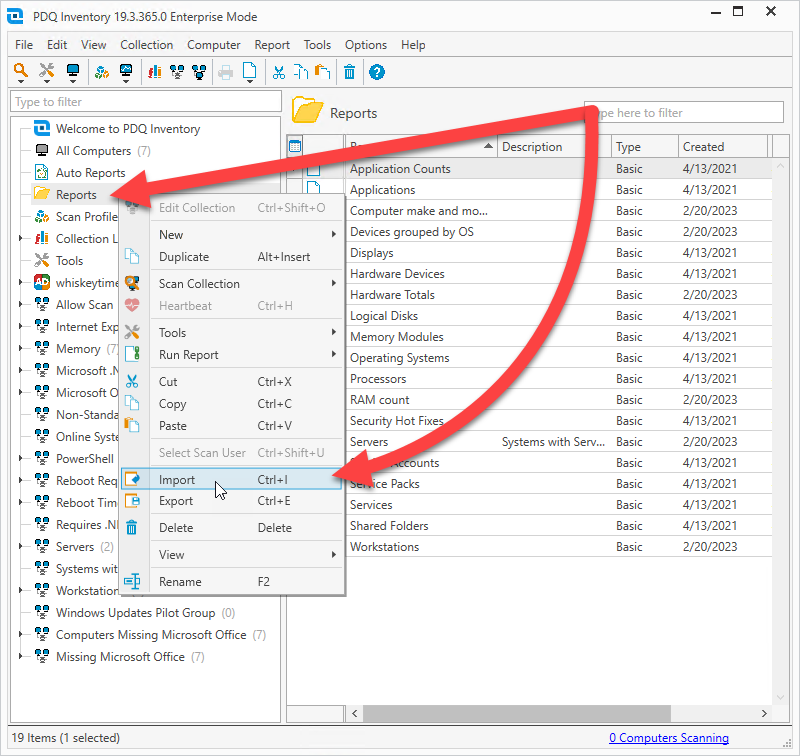
Right-click on the Reports button in PDQ Inventory, then click Import.
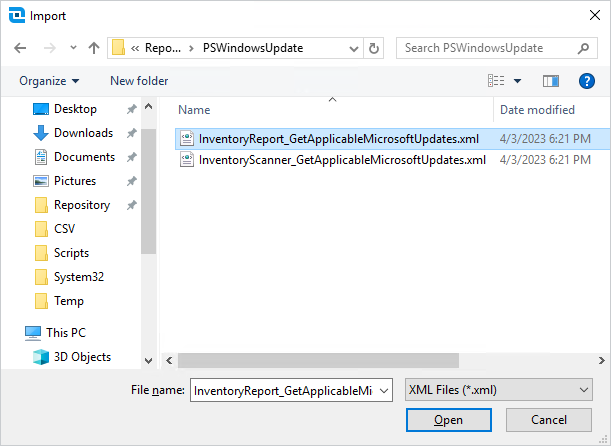
Browse to the report XML located at $(Repository)\PSWindowsUpdate\InventoryReport_GetApplicableMicrosoftUpdates.xml
Select the XML, then click Open.
Once the XML has been imported, you’ll find the Get Applicable Microsoft Updates report under the Reports option in Inventory.
The Get Applicable Microsoft Updates report is a great way to quickly identify which devices are missing updates.
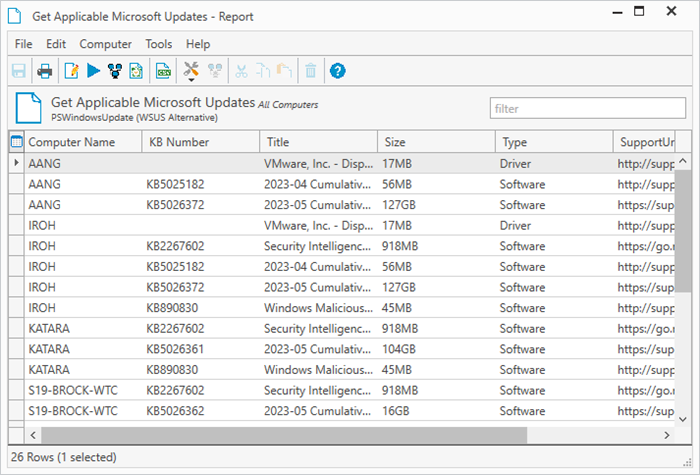
Remember: You can right-click on columns to group the report by that column. Grouping the report by computer name or KB can make the report easier to read.
Windows updating made easy
Sure, you could use an outdated system to deploy your Windows updates. Or you could take the guesswork out of patch management by using PDQ Deploy and Inventory — or PDQ Connect. With rapid deployments and accessible insights, PDQ simplifies complicated tasks. And couldn’t we all use a little more simplicity in our lives? Try out PDQ Deploy and Inventory with a 14-day free trial. If you’re looking for an agent-based solution to manage your remote endpoints, try out PDQ Connect.














