On Patch Tuesday we discussed CVE-2021-31166 being a potentially wormable exploit based on the information we had at the time. Well, fast forward a week, and not only do we now know it is wormable, but there is proof of concept code out there. This makes an already dangerous exploit downright scary. If you are still in your testing window, it might be wise to bump up your deployment to get secured ASAP.
Luckily, among the doom and gloom of this news, there is a slight silver lining. Two elements are needed for this vulnerability. The first is that an HTTP listener needs to be used on the machine. This could be either external-facing like IIS or something internal like WinRM. This exploit attacks the HTTP listener (HTTP.sys) and allows the attacker to send a specifically crafted packet that will allow an unauthenticated user to either run malicious code, or do a denial of service on the machine. The second is that it needs to be on the latest builds 2004 and 20H2 versions of Windows and Windows Server.
Finding At-Risk Machines
Update: Thank you to Craig at Pacific Office Automation for pointing out that the collection I had would find all eligible machines, but would not exclude them as they get updated. We have updated the collection to correct this by adding a Not Any Hotfix contains KB5003173. Now it won't only tell you who is at risk, but also give you some peace of mind that you are fully protected after patching.
Now that we know which machines are at risk, finding those in your environment should not be an issue with PDQ Inventory. A dynamic collection that Looks for O/S Version not Lower than 10.0.19041.98 and Does not contain KB5003173 should gather all machines, and remove them as you get them patched. If you are only worried about external-facing machines you could add a section looking for Windows Feature iis.
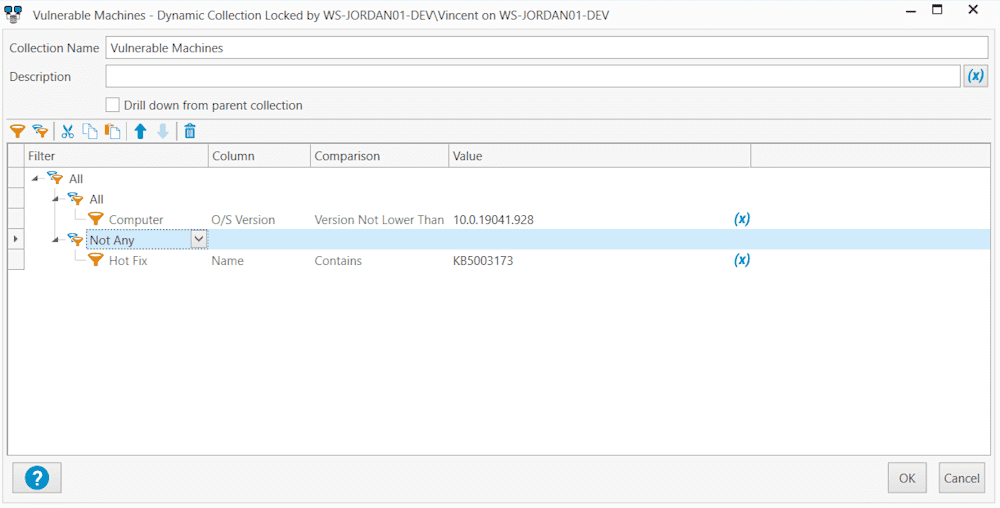
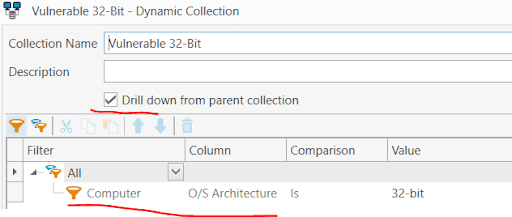
If you would like to separate these by 32 or 64-bit architecture, you can build a sub-collection with a filter for architecture, and the check box to drill down from the parent collection.
Patching Machines
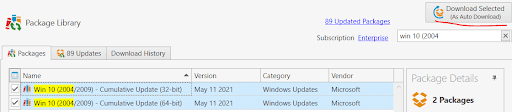
Patching these machines is going to be even easier. Both 2004 and 20H2 are patched with the same Microsoft KB, so we should only need one package per architecture from PDQ Deploy.
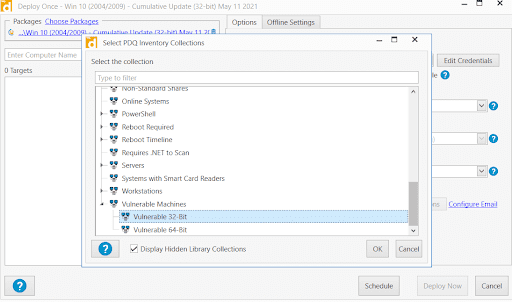
Deploy the new package against the collections we just built, and your system will be safe once again.
Conclusion
While the pool of at-risk machines might be limited, the threat they represent is massive. Hopefully you have already patched. If you are still in testing phase, I recommend moving up your timeline for production patching to now. With the Proof of concept out, exploitation will not be far behind. If you are looking for a quick way you can get patched right away, PDQ Deploy and PDQ Inventory can be set up and patching your system within minutes.