We've got a live one, folks. If you're a Dell shop, buckle up because this ride might get a little bumpy. The security research firm SentinelLabs has found five high severity flaws in Dell's firmware update driver. The driver, which comes pre-installed on most Dell machines, has been in use since at least 2009, meaning this driver is most likely installed on millions if not hundreds of millions of Dell computers. So if you have a Dell or manage Dell computers, you are most likely affected by these vulnerabilities and will need to take action.
On The Loose For 12 Years
The specific driver in question is dbutil_2_3.sys. The driver is responsible for Dell Firmware Updates via the Dell Bios Utility and is installed on desktops, laptops, and tablets and can be found on both personal and enterprise-level equipment. Kasif Dekel, the security researcher who discovered the vulnerabilities, was alerted to the driver using the application Process Hacker, which can notify users as processes get created or deleted. This led Kasif to discover five separate vulnerabilities. Four of these vulnerabilities, if exploited, can lead to an elevation of privileges from a non-administrator to kernel mode privileges and another code logic issue that can result in a denial of service. All five of these vulnerabilities are being tracked under one CVE, which is CVE-2021-21551. Dell goes into more detail about the affected drivers and systems on this Dell Security Advisory DSA-2021-088 page.
Locating Affected Machines With PDQ Inventory
This may come as a shock to some, but the first thing Dell recommends doing is to remove the affected driver. I know, crazy. Luckily, with the help of PDQ Inventory, we can quickly scan our environment for affected devices. Dell has listed the following locations to check for the driver file:
C:\Users\<username>\AppData\Local\Temp\
and
C:\Windows\Temp
Since we know where to narrow down our search, we can create a Files & Directories scanner to search for devices that have the culprit file.
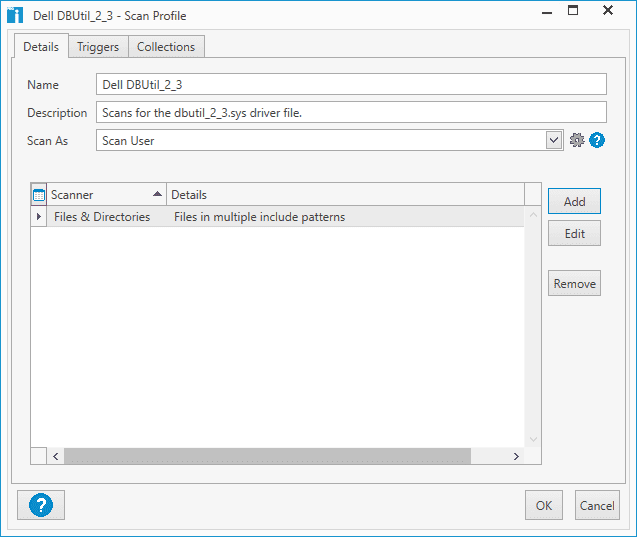
With PDQ Inventory open, click Scan Profiles.
Click New
Give your new scan profile a descriptive name
Click Add
Click Files & Directories
Make sure File is selected for the Type, then add these two entries into the Include Pattern(s) field.
%windir%\Temp\DBUtil_2_3.sys %systemdrive%\Users\**\AppData\Local\Temp\DBUtil_2_3.sys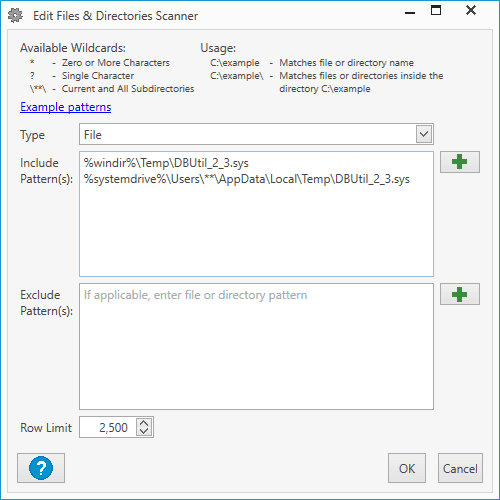
Click OK
Click OK at the Scan Profile window
With our scanner created, we can now run it against our computers. Right-click on All Computers, then click Scan Collection > "New Scanner Name"
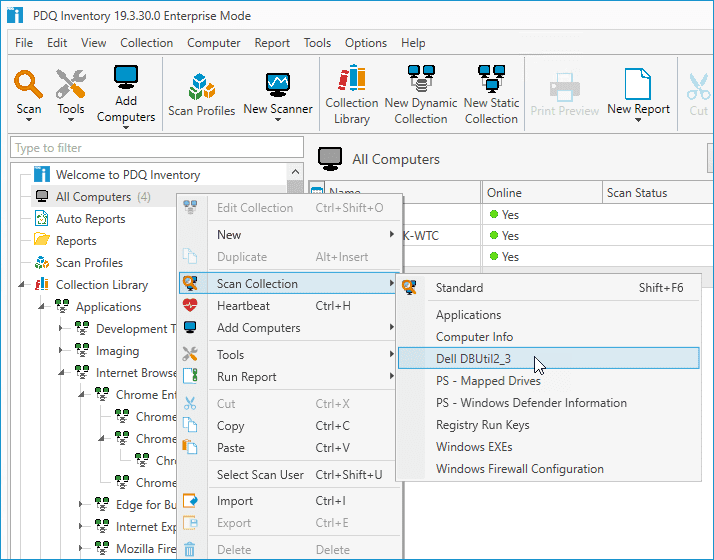
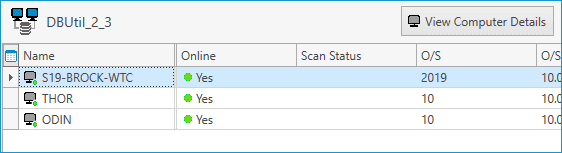
Once the scanner starts, you can view the scan status of each computer in the All Computers view.
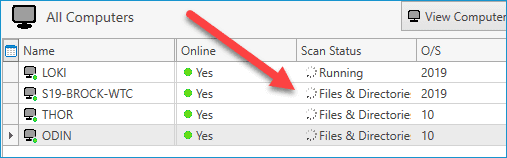
Once the scan completes, double-click on any computer to open the computer details window. Next, click on the Files & Directories menu item to view the results of the scan.
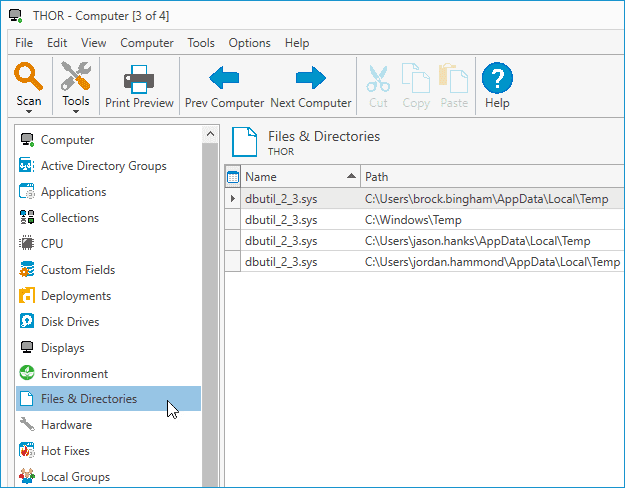
As you can see in the above image, the scan found the file in four locations on this computer.
Creating A Dynamic Collection Of Computers With The Driver File
Before we remove the file from the affected computers, we want to make sure we only target the devices that have the dbutil_2_3.sys file. We don't want to waste bandwidth and resources trying to remove the file from computers that don't have it. The easiest way to do this is to create a dynamic collection in PDQ Inventory.
With PDQ Inventory open, click New Dynamic Collection
Enter a descriptive name for the collection
Add the following filter: Files & Directories > Name > Contains > dbutil_2_3.sys
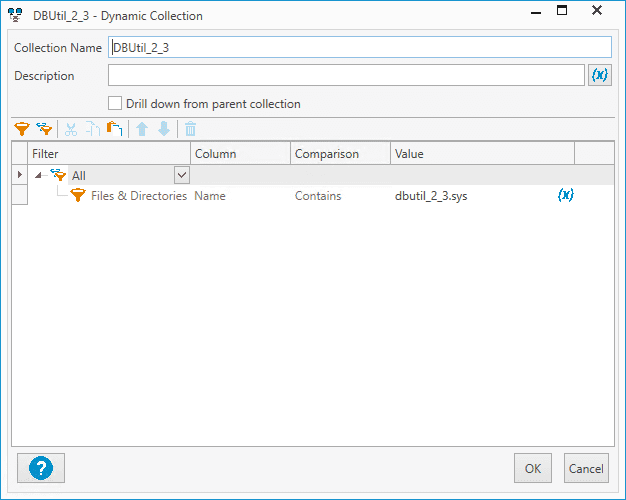
Click OK
The new dynamic collection should appear in the menu with the rest of your dynamic collections, and it should give you a number of how many computers are members of the collection
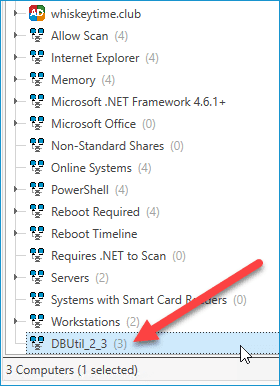
Clicking on the collection should give you the list of all the computers that contain the driver file
Using PowerShell And PDQ Deploy To Remove The Files
Alright, now that we've got our computers neatly organized into a dynamic collection, we can proceed to remove the vulnerable files with extreme prejudice. With PDQ Deploy, we can build and deploy a PowerShell package that checks for the files and terminates them.
With PDQ Deploy open, click New Package
Give your package a worthy name
Click New Step > PowerShell
Add the following PowerShell script:
$list = "$env:HOMEDRIVE\Users\*\AppData\Local\Temp", "$env:SystemRoot\Temp" Foreach ($location in $list){ Remove-Item $location -Recurse -Include dbutil_2_3.sys }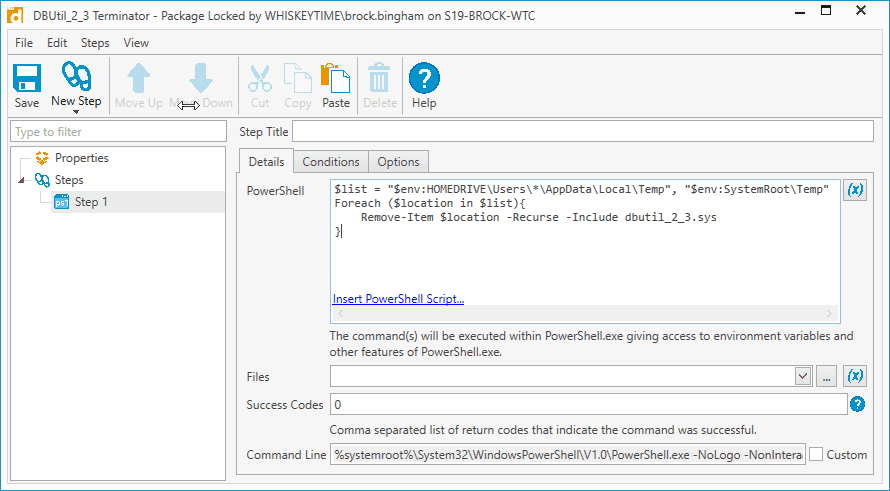
Now let's add a scan step to ensure the file is removed after the script runs. Click New Step > Scan
For the Scan Profile, select the scan profile we created in PDQ Inventory
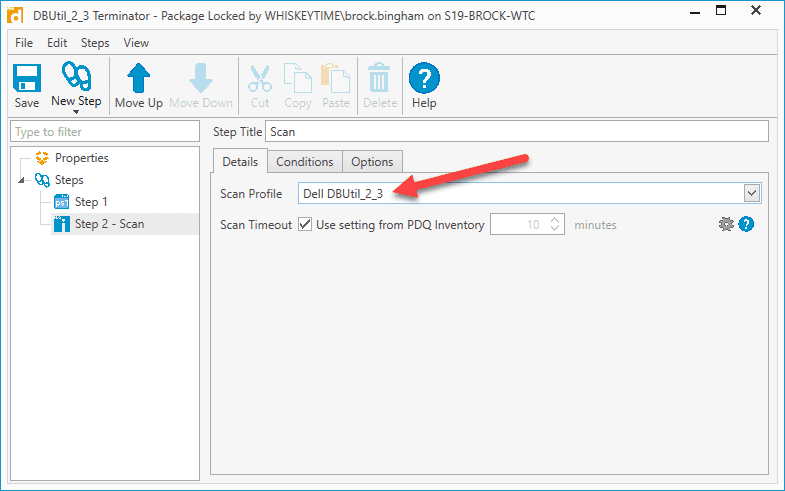
Click Save
Now that our package has been created let's first test it out to ensure it's working correctly before deploying it to all affected machines.
Right-click on the package and click Deploy Once
Enter a computer that you know has the driver file
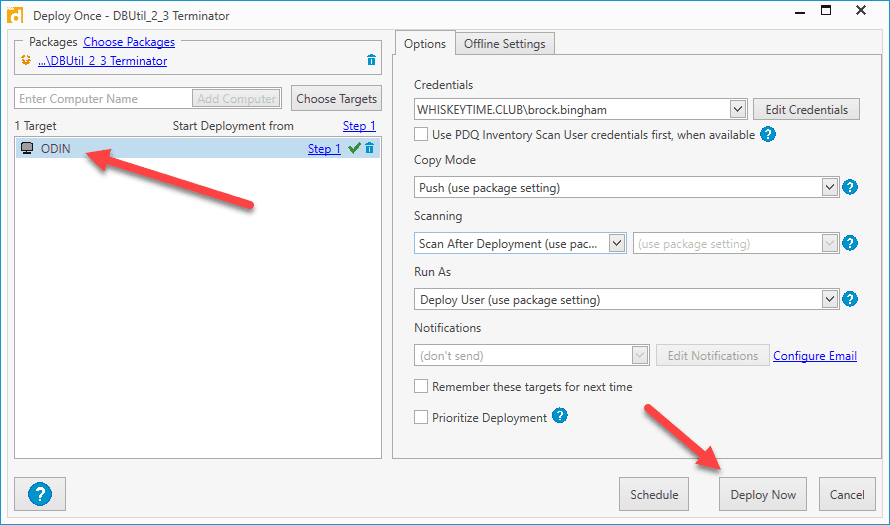
Click Deploy Now
PDQ Deploy will send out the package, which will remove the files from the machine you selected. Once the deployment is complete, the computer will be scanned to ensure the file was removed. If everything is successful, you can send the package out to a broader test group, or, if you've got more faith than George Michael's 1987 hit song, then go ahead and deploy that package to the entire dynamic collection. Follow the same steps as above, except for step 2, select Choose Targets > PDQ Inventory > Collection, then select the dynamic collection we created in PDQ Inventory and click OK.
Once the deployment finishes, check the dynamic collection in PDQ Inventory to ensure that all of the computers had the files removed successfully. If some devices were offline and didn't receive the package, you can create a schedule with a heartbeat trigger in PDQ Deploy, sending the package out to those missed computers as they come online. You can find out more about creating schedules with dynamic collections and heartbeat triggers in this blog post.
Wrapping Up
After removing the files, Dell recommends obtaining and running a remediated firmware update utility package to keep the vulnerable driver from returning in an accidental update in order to perform a dell security advisory update silent install. You can find out more about the utility needed for your systems on the Dell Security Advisory DSA-2021-088 page.
PDQ Inventory and PDQ Deploy make scanning for and removing vulnerable files from your systems a walk in the park. If you don't already use PDQ Inventory and PDQ Deploy, go download our free 14-day trial. If you manage hundreds or even thousands of Dell machines, now's the perfect time to try out our products.