Passing credentials in PowerShell scripts is risky if you store passwords in plain text. Instead, you can encrypt passwords and use SecureStrings or PSCredential objects to protect sensitive data while still supporting automation.
What are PowerShell SecureStrings?
A SecureString in PowerShell is an encrypted object that stores sensitive information, such as passwords, to prevent exposure during PowerShell script execution.
Syntax
ConvertTo-SecureString [-String] SomeString
ConvertTo-SecureString [-String] SomeString [-SecureKey SecureString]
ConvertTo-SecureString [-String] SomeString [-Key Byte[]]
ConvertTo-SecureString [-String] SomeString [-AsPlainText] [-Force]
ConvertFrom-SecureString [-SecureString] SecureString [-SecureKey SecureString]
ConvertFrom-SecureString [-SecureString] SecureString [-Key Byte[]]–String String
The string to convert to a SecureString.
–SecureKey SecureString
Encryption key as a SecureString.
–Key Byte[]
Encryption key as a byte array.
SecureString isn't the only way to manage your secrets.
You can also learn how to manage PowerShell secrets with the SecretsManagement module.
Store the credential as a SecureString
Get-Credential and Read-Host
Use Get-Credential to create a PSCredential object that stores a username and SecureString password. This object can be passed into any cmdlet that supports PSCredential authentication.
$MyCredential = Get-Credential
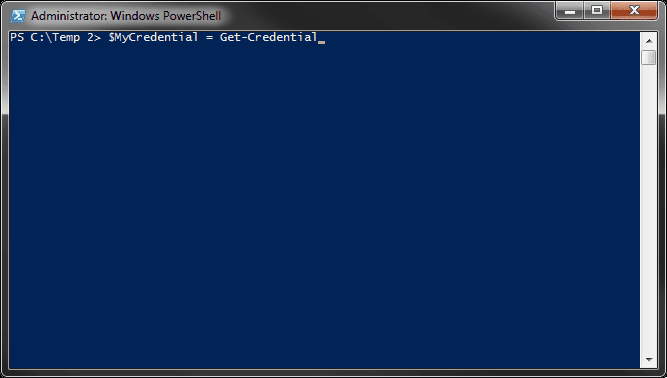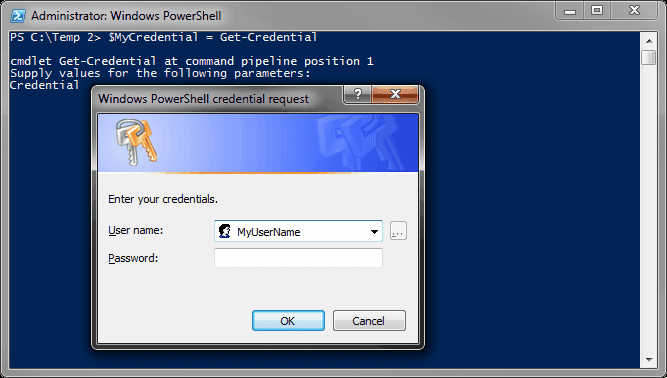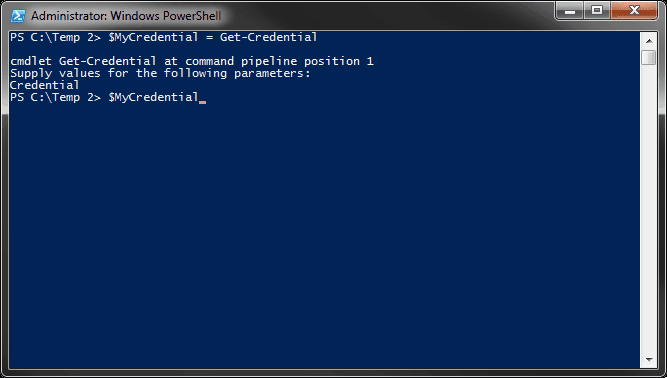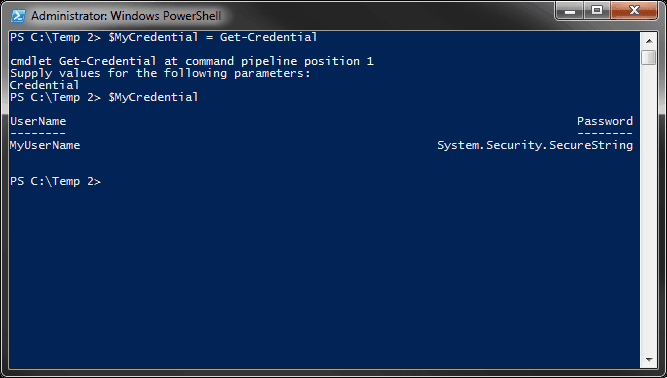
Notice that when you access the variable $MyCredential, you are able to see the username but not the password. It only displays "System.Security.SecureString" on the screen. This is because the password is now stored as a SecureString.
You can then use this new PSCredential object with cmdlets that support PSCredential objects. You can also individually reference the username or the password for cmdlets that don’t accept a PSCredential object but support username and password parameters.
In those cases, you can use $MyCredential.Username and $MyCredential.Password.
Or you can use Read-Host to prompt for input and store the result in a variable. This includes prompting for a SecureString (for a password).
$user = Read-Host "Enter Username"
$pass = Read-Host "Enter Password" -AsSecureString
The output is very similar to the output of the Get-Credential variable we used, $MyCredential. It shows the username as "MyUserName" and the password as "System.Security.SecureString."
This is great for manual runs of scripts since it helps to remove the password from the script, but it doesn’t really help with our automation. We’re looking for a solution that can run automatically without having to constantly supply credentials via Get-Credential/Read-Host or by leaving our passwords in plain view for anybody to read.
Encrypt passwords and other strings
ConvertTo-SecureString
Use ConvertTo-SecureString to turn a plain text string into a SecureString. This lets you securely store or pass passwords into PSCredential objects or other cmdlets.
Syntax:
ConvertTo-SecureString [-String] SomeString
ConvertTo-SecureString [-String] SomeString [-SecureKey SecureString]
ConvertTo-SecureString [-String] SomeString [-Key Byte[]]
ConvertTo-SecureString [-String] SomeString [-AsPlainText] [-Force]
–String String
The string to convert to a SecureString
–SecureKey SecureString
Encryption key as a SecureString.
–Key Byte[]
Encryption key as a byte array.
–AsPlainText
Tells command to treat string as plain text. The string is not encrypted when
using this command. Because of the lack of security, the -Force parameter
is also required.
–Force
Confirms you understand the lack of security when using -AsPlainTextWhen you are not using the –Key or –SecureKey parameters, PowerShell uses the Windows Data Protection API to encrypt/decrypt your strings. This effectively means that only the same user account on the same computer can use this encrypted string. That is something to keep in mind as you attempt to automate any scripts. If you’re using a service account, you’ll need to use the –Key or –SecureKey parameters.
Let’s say you want to take the text “P@ssword1” and convert it to a SecureString. Since this is a plain text string, we’re going to use the –AsPlainText and –Force parameters.
"P@ssword1" | ConvertTo-SecureString -AsPlainText -ForceThe result is a SecureString object. Unfortunately, you cannot save a SecureString object to a file for later use. You have to convert this SecureString object to an encrypted standard string. You can do this with ConvertFrom-SecureString.
Save encrypted standard strings
ConvertFrom-SecureString
Use ConvertFrom-SecureString to convert a SecureString into an encrypted string that can be saved to a file for later retrieval. You can use the command directly or pipe results into the command.
Syntax:
ConvertFrom-SecureString [-SecureString] SecureString
ConvertFrom-SecureString [-SecureString] SecureString [-SecureKey SecureString]
ConvertFrom-SecureString [-SecureString] SecureString [-Key Byte[]]
–String String
The string to convert to a SecureString
–SecureKey SecureString
Encryption key as a SecureString.
–Key Byte[]
Encryption key as a byte array.Following the same example above, we’ll take the output of the previous example and pipe it into the ConvertFrom-SecureString command to get an encrypted standard string.
"P@ssword1" | ConvertTo-SecureString -AsPlainText -Force | ConvertFrom-SecureString
The result is an encrypted standard string that you can save for later retrieval.
SecureString examples
We now know how to convert a SecureString to an encrypted standard string. We can take any method we like to get a SecureString, convert it to a standard string, and then save it to a file. This won't stop anybody who knows what they’re doing from decrypting the password or reusing the encrypted password if they ever compromise your login. The whole point of converting your password to a SecureString and storing it in a file is to keep it out of plain text in your scripts so that it’s not as easily discovered. It’s not foolproof, but it’s pretty good.
When you're not specifying a key or SecureKey, this only works for the same user on the same computer can decrypt the encrypted string. Any process running under that user account on the same machine can also decrypt it.
Here is an example of each:
Export SecureString from plain text with Out-File
"P@ssword1" | ConvertTo-SecureString -AsPlainText -Force | ConvertFrom-SecureString | Out-File "C:\Temp 2\Password.txt"
Export SecureString from Get-Credential
(Get-Credential).Password | ConvertFrom-SecureString | Out-File "C:\Temp 2\Password.txt"
Export SecureString from Read-Host
Read-Host "Enter Password" -AsSecureString | ConvertFrom-SecureString | Out-File "C:\Temp 2\Password.txt"Any one of these examples should provide you with a Password.txt file that has an encrypted standard string the represents the password.
When you need to use this encrypted password, you simply reverse the process by importing the data from your file and use ConvertTo-SecureString. If all you need is a SecureString, you can stop there. You could even take it a step further and create a PSCredential object.
Create SecureString object Get-Content and ConvertTo-SecureString
$pass = Get-Content "C:\Temp 2\Password.txt" | ConvertTo-SecureString
Create PSCredential object
$User = "MyUserName"
$File = "C:\Temp 2\Password.txt"
$MyCredential=New-Object -TypeName System.Management.Automation.PSCredential `
-ArgumentList $User, (Get-Content $File | ConvertTo-SecureString)Easily run PowerShell scripts on remote devices
Need to run your awesome PowerShell scripts on remote devices? PDQ Connect can easily execute PowerShell scripts on any managed device with an active internet connection.
Share credentials across machines or users
By default, SecureStrings use the Windows Data Protection API (DPAPI), which only works for the same user on the same computer. To share credentials across machines or accounts, use a Key or SecureKey with AES encryption.
When you use a Key/SecureKey, the Advanced Encryption Standard (AES) encryption algorithm is used. You are able to use the stored credential from any machine with any user as long as you know the AES Key that was used.
Using no Key/SecureKey
First, let’s show an example of what you'll see if you try to create a credential from one machine (Machine 1) and then access it from another machine (Machine 2) without providing a key.
Encrypting a password without a key and saving it to file from Machine 1
This creates the file Password.txt with an encrypted standard string representing the password. It uses DPAPI.
$File = "\\Machine1\SharedPath\Password.txt"
$Password = "P@ssword1" | ConvertTo-SecureString -AsPlainText -Force
$Password | ConvertFrom-SecureString | Out-File $FileAccessing the encrypted password file from Machine 1
This successfully gets the encrypted standard string using Get-Content and converts it to a SecureString.
$File = "\\Machine1\SharedPath\Password.txt"
Get-Content $File | ConvertTo-SecureString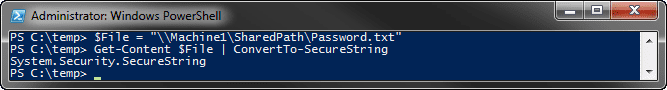
Accessing the encrypted password file from Machine 2
This fails with an error indicating that the key is invalid. Example below:
$File = "\\Machine1\SharedPath\Password.txt"
Get-Content $File | ConvertTo-SecureString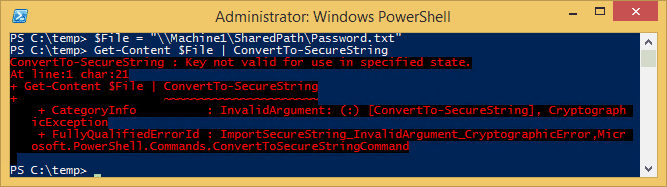
Using Key/SecureKey
Now, let's show a simple example of creating an encrypted standard string with the use of a key. AES encryption only supports 128-bit (16 bytes), 192-bit (24 bytes) or 256-bit key (32 bytes) lengths, so we'll need to create or generate an appropriate key. For simplicity, let's create a simple byte array of ascending numbers. We'll use a 128-bit key, so we'll need a 16-byte array.
Long way
[Byte[]] $key = (1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16)Short way
[Byte[]] $key = (1..16)Encrypting a password and saving it to file from Machine 1
This creates the file (with Out-File) Password.txt with an encrypted standard string representing the password. It uses AES.
$File = "\\Machine1\SharedPath\Password.txt"
[Byte[]] $key = (1..16)
$Password = "P@ssword1" | ConvertTo-SecureString -AsPlainText -Force
$Password | ConvertFrom-SecureString -key $key | Out-File $FileAccessing the encrypted password file from Machine 1
This successfully gets the encrypted standard string and converts it to a SecureString. It uses the AES key that we provided earlier.
$File = "\\Machine1\SharedPath\Password.txt"
[Byte[]] $key = (1..16)
Get-Content $File | ConvertTo-SecureString -Key $key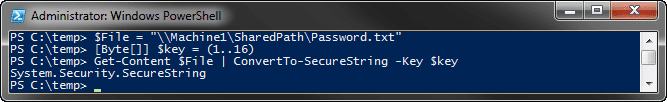
Accessing the encrypted password file from Machine 2
This successfully gets the encrypted standard string and converts it to a SecureString by using the AES key.
$File = "\\Machine1\SharedPath\Password.txt"
[Byte[]] $key = (1..16)
Get-Content $File | ConvertTo-SecureString -Key $key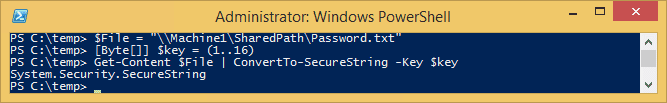
AES key examples
When using AES keys with SecureStrings, protect the key file as securely as the password itself. Anyone with access to the key can decrypt the stored credentials.
In my previous example, I used a very simple 16-byte array that is stored in the body of the script itself. This is not a good practice and is essentially the same as if you were to write the plain text password. Alternatively, you could create/generate a key beforehand in a separate script.
As an example, I have built a small script to generate a random 16-byte array. I have used the System.Security.Cryptography.RNGCryptoServiceProvider class to fill a byte array with randomly generated data.
Create AES key with random data and export to file
$KeyFile = "\\Machine1\SharedPath\AES.key"
$Key = New-Object Byte[] 16 # You can use 16, 24, or 32 for AES
[Security.Cryptography.RNGCryptoServiceProvider]::Create().GetBytes($Key)
$Key | out-file $KeyFileCreate SecureString object
$PasswordFile = "\\Machine1\SharedPath\Password.txt"
$KeyFile = "\\Machine1\SharedPath\AES.key"
$Key = Get-Content $KeyFile
$Password = "P@ssword1" | ConvertTo-SecureString -AsPlainText -Force
$Password | ConvertFrom-SecureString -key $Key | Out-File $PasswordFileCreate PSCredential object
$User = "MyUserName"
$PasswordFile = "\\Machine1\SharedPath\Password.txt"
$KeyFile = "\\Machine1\SharedPath\AES.key"
$key = Get-Content $KeyFile
$MyCredential = New-Object -TypeName System.Management.Automation.PSCredential `
-ArgumentList $User, (Get-Content $PasswordFile | ConvertTo-SecureString -Key $key)That’s it! You can use the key file to decrypt the password file from any machine with any user.
Be sure to protect that AES key as if it were your password. Anybody who can read the AES key can decrypt anything that was encrypted with it.
At the very least, you should implement strict NTFS access controls for both your password and key files. This should keep out most prying eyes. Additionally, you may consider storing the data in a database with strict access controls or even implementing public-key (asymmetric) cryptography for additional control.
In any case, you should be good to use AES keys with your SecureStrings now.