Architecture overview
Introduction to PDQ Connect
PDQ Connect is a web-based device management tool. IT professionals and sysadmins use PDQ Connect to remotely manage the devices in their organization. IT professionals perform actions like scanning endpoints for device information, organizing devices, updating software, or running scripts on devices — all remotely through the internet.
To remotely manage devices, PDQ Connect uses a proprietary agent, developed by PDQ, that sysadmins install on the Windows devices that need to be managed. Once this agent software is installed locally on a device, device information is streamed in real time to the PDQ Connect administrator portal using a secure HTTPS WebSocket. An IT professional can use the online administrator portal to view, edit, organize, and manage their devices.
Product architecture
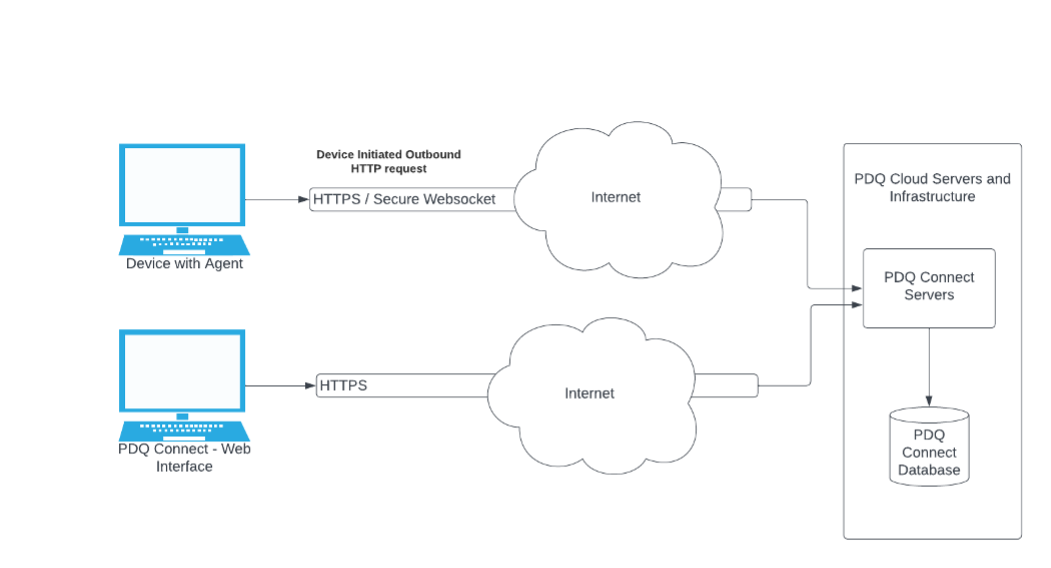
PDQ Connect works over the internet using installed agent software that can run on supported Windows devices. The agent software uses HTTPS and secure WebSockets to initiate a request from managed devices to PDQ’s server infrastructure over the device’s internet connection.
When Connect is used to run device scans and deploy software using the Connect web interface, PDQ’s servers will securely save those requested tasks in the Connect database system. When a device running the PDQ Connect Agent is connected to the internet, it will make an outbound HTTP request to PDQ servers to get any pending tasks.
PDQ Connect Agent
To manage a Windows device using PDQ Connect, an administrator must first install the PDQ Connect Agent on the device.
The agent software runs in the background on your Windows devices and is responsible for running periodic scans for device information, such as uptime, drive capacity, and installed software. It runs with administrator permissions so that it can perform admin-required package installations and other maintenance activities.
When you use Connect to deploy software, the agent software running on the device reaches out to PDQ’s servers over a secure internet connection to receive the package installation instructions. It communicates using both industry-standard HTTPS and WebSocket protocols and certificates to keep scan and deployment information private, and cryptographic signatures are used to ensure that the deployment instructions have not been tampered with.
Some packages may use non-encrypted HTTPS download URLs, primarily when HTTPS URLs are not provided by package providers. In cases where encrypted HTTPS URLs are not used, a secure cryptographic hash is used to ensure that the package asset files are not tampered with.
Learn more about the PDQ Connect Agent.
PDQ Connect Admin Web Console
Administrators use the PDQ Connect Admin Web Console to configure computers, create packages, and update computers. The Admin Web Console is hosted and provided by PDQ as part of a paid subscription.
When interacting with PDQ Connect through the web console in a browser, all communications to and from PDQ Connect are encrypted using industry standard HTTPS connections using valid certificates.
The web console is where administrators can see information about the devices they manage, as well as create and observe package deployments. When packages are deployed to devices, the setup and configuration options of that deployment are sent over that secure connection to PDQ’s servers and saved into the PDQ Connect database. Then they are delivered to the devices as soon as possible.
Data security
Encryption
At rest:
Your information and the information about your end users and devices is securely encrypted by Connect’s servers. That includes all device scan information, deployment logs and statistics information, and custom packages you upload to Connect using the web console, as well as any other data stored in PDQ’s database. All of this data is encrypted at rest.
In transit:
All information traveling between your browser and the PDQ Admin Web Console is encrypted in transit using HTTPS TLS. We also use HTTPS TLS encryption for secure communication between the Connect Agent software and PDQ’s servers.
Please note that while the contents of any custom packages are encrypted in transit to a device, if user-created scripts or installers initiate other web requests or downloads, it is the user’s responsibility to ensure that those are done securely.
Data isolation
All data within the PDQ Connect databases and services are logically separated and isolated using unique company identities. When data is requested from a service or database, it is isolated to only data that the unique companyID is allowed to access. This means that customers only see their own data and never data from other PDQ Connect customers.
Data backups
All critical data is backed up at least daily. Annual tests are performed to ensure data backups can be restored successfully.
Data hosting
Connect's database servers are currently hosted in the US in Google Cloud Platform's us-central1 region. Packages and report data managed by PDQ are currently hosted on Cloudflare in one or more North America regions.
Identity and authentication
Identity and authentication overview
PDQ Connect utilizes industry-leader authentication and identity provider Auth0 for authentication and password management. PDQ Connect does not collect, process, or use passwords directly. Organizations have the option to choose between using SSO or username/password for authentication. All accounts are required to use multifactor authentication.
You can manage organization-wide settings, as well as a number of customizable options for each user. You have the option to enable methods for Passwordless with Email, Google SSO, Microsoft SSO, or your own authentication provider using OIDC.
MFA options include SMS, authenticator apps, and WebAuthn. These options can be enabled or disabled, and MFA can be enforced at the organization level for all users in your organization. MFA is enforced by default.
Single Sign-On (SSO)
Organizations can optionally use Single Sign-On (SSO) to authenticate with and access their PDQ Connect account. By utilizing this method, users do not have a set username and password with PDQ. Instead, they leverage their existing accounts to access PDQ Connect. Existing SSO options are Google, Microsoft Live, Microsoft Azure AD, and bring your own OIDC provider. SSO authentication is the recommended option for managing authentication.
Multifactor authentication (MFA)
Multi factor authentication is required by default for all organizations. Authentication method options include: Passwordless with email, OIDC, Google, and Microsoft.
For organizations that enable the OIDC, Google, and/or Microsoft authentication methods, the admin has the option to disable requiring MFA for their users. PDQ recommends that MFA be enabled by an external provider in this instance.
Account retrieval
Organizations control and manage who has access to the PDQ Connect Admin Web Console. Administrators can create users, edit user permissions, or remove users from their organization from the account manage pages at portal.pdq.com. PDQ does not manage users or access on behalf of customers.
Multi-factor Authentication (MFA) reset
Users can initiate the MFA reset process by clicking the “Reset MFA Configuration” link during the MFA verification step of the login process.
If a user is the sole administrator or owner of an account, they will need to contact support to reset their MFA configuration. If the user is associated with multiple accounts and is also the sole admin for any of them, they must obtain approvals from all associated accounts in addition to contacting support.
The reset is considered complete once an admin from each account associated with the user has approved it, and the user’s MFA configuration will be reset. Upon the user’s next login after the reset is complete, they will be prompted to set up a new MFA method.
Account restoration
For security reasons, PDQ cannot restore access to an account where an administrator left an organization or forgot their username. In these instances, PDQ recommends that organizations restore the inbox or account of administrators.
Operational security
System access
PDQ enforces a principle of least privilege policy over defined subjects and objects. PDQ controls access based upon defined roles and users authorized to assume such roles. By doing so, PDQ ensures that user access to in-scope system components is based on job role and function.
PDQ ensures that, at minimum, the principle of least privilege policy establishes and enforces access on the following elements:
Core business suite
Software development system
Cloud service providers (CSP)
Other business critical systems
Vulnerability prevention
PDQ has established a Vulnerability Monitoring and Scanning Program designed to monitor and scan for internal and external vulnerabilities in systems and hosted applications at least weekly (or more randomly) to identify, quantify, and prioritize vulnerabilities. PDQ also identifies and implements code analysis tools in the organization’s development pipeline to regularly scan both static and dynamic codebases to check for vulnerabilities. Processes ensure that the scope of any vulnerability is defined and documented prior to the initiation of a vulnerability assessment.
PDQ also ensures that all findings from vulnerability scans are analyzed and documented on a weekly basis and are remediated in accordance with the organization's risk tolerance. PDQ shares information obtained from the vulnerability monitoring process and control assessments with key stakeholders to help eliminate similar vulnerabilities in other systems.
Application security
Managing users
Administrators on a customer’s account have the ability to add, remove, and edit users within their account.
Managing feature access
Features within the PDQ Connect product can be enabled or disabled for users by the Administrators on an account. Administrators can create roles, assign feature access settings to a role, and then assign the role to a user. Users can only access the features specified by their assigned role. Administrators can specify a default role that all newly created users get automatically assigned to.
Other security topics
Third-party vendors
PDQ Connect utilizes a handful of services that are required to provide product functionality. These third-party vendors process data for PDQ.
Provider | Service | Notes |
|---|---|---|
Auth0 | Authentication | Used for managing user authentication and passwords. |
Mixpanel | Usage tracking | Used for tracking feature usage in PDQ Connect. |
Stripe | Payments | Used for managing subscriptions and storing payment information. |
LaunchDarkly | Feature enabling | Used for enabling or disabling certain product features |
Mouseflow | Usage tracking | Used for tracking mouse locations and feature using |
ISL Online | Remote desktop | Used for remote desktop functionality within Connect |
GCP | Cloud hosting | Used for hosting the components that make up Connect |
Cloudflare | Website security | Used for protecting network connections to and from Connect |
Security audits
PDQ performs annual human-based and monthly automated penetration tests to identify vulnerabilities that could be exploited to gain access to its production environment. PDQ Corporation will ensure that in-scope assets are documented prior to the initiation of any penetration test. PDQ’s internal Connect team has committed to an internal SLA to remediate issues found by these tests.
Additionally, PDQ has engaged a third-party bug bounty program that pays out for non-publicly disclosed vulnerabilities.
Certifications
PDQ takes security seriously and realizes the value of independently audited security certifications. We are SOC 2 compliant and will continue to undergo routine audits for updated reports.
Package Library
PDQ Connect offers an optional feature called the Package Library. This feature allows organizations to pull packages for popular applications from PDQ — without having to manage the packages themselves. For example, PDQ keeps the latest version of Chrome available in the Package Library, making it easy for organizations to deploy the latest browser version to target devices.
This is an optional feature included with PDQ Connect. Organizations can choose to not use this feature and instead manually create packages.
Package creation process
To create a software package, a proprietary PDQ system periodically scans software providers for new updates and downloads them to the PDQ package repository. As available, PDQ submits the hashes for these products to a third-party site for reputation analysis, which leverages multiple antivirus engines.
All packages are built using a secured virtual machine that is dedicated for the creation of packages. Once a package has been built, it is manually tested with a group of virtual machines, each having a different version of Windows installed. Each machine is then analyzed to ensure a successful deployment. Furthermore, each package is tested on an additional device that utilizes both antivirus signatures and behavior-based scanning to ensure each package is secure and virus free.
This process is manually verified by a secondary engineer for quality assurance. At no point can a single engineer build and publish into the library. Once the package passes secondary validation, the package is uploaded to the package library and made available in PDQ products.
The packages available in the PDQ Package Library can be found here.
Custom packages
Customers can optionally create their own packages and upload their own software to PDQ Connect. PDQ does not share, or make available, custom packages created by one customer with other PDQ Connect customers. It is the responsibility of customers to ensure the packages they create are safe.


